Sommaire
Cryptography
aes-but-twice
Statement :
AES-CTR is pretty secure! So is CBC. Plus those cosmic rays are really messing up my ciphertexts. What if i encrypt with both?
Code :
#!/usr/local/bin/python
if __name__ != "__main__":
raise Exception("not a lib?")
import os
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad, unpad
from Crypto.Util import Counter
nonce = os.urandom(8)
iv = os.urandom(16)
key = os.urandom(16)
CTR_ENC = AES.new(key, AES.MODE_CTR, nonce=nonce)
CBC_ENC = AES.new(key, AES.MODE_CBC, iv=iv)
def ctr_encrypt(data):
return CTR_ENC.encrypt(pad(data, 16)).hex()
def cbc_encrypt(data):
return CBC_ENC.encrypt(pad(data, 16)).hex()
flag = pad(open("flag.txt", "rb").read(), 16)
print(ctr_encrypt(flag))
print(cbc_encrypt(flag))
print(nonce.hex())
while True:
try:
inp = input()
if inp == "exit":
break
data = bytes.fromhex(inp)
print(ctr_encrypt(data))
print(cbc_encrypt(data))
except Exception:
pass
Discovery :
The flag is padded first when it is read from the file.
flag = pad(open("flag.txt", "rb").read(), 16)
So, the variable flag is a multiple of 16 bytes.
And, the flag is encrypted with AES-CTR and AES-CBC.
def ctr_encrypt(data):
return CTR_ENC.encrypt(pad(data, 16)).hex()
As we can see, the data is padded a second time before being encrypted.
So, the data looks like this :
flag{xxxxxxxxxxxxxxxxxxxx}\x06\x06\x06\x06\x06\x06\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10
The first group of \x06 is added by the padding of the flag, and the second \x10 is added by the padding of the data before encryption.
So, we know the last block of the flag, is \x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10
Morevover, for entire program, the objects CTR_ENC and CBC_ENC are the same, so if we encrypt new data, it's added to the previous data. Explanation :
CTR_ENC = AES.new(key, AES.MODE_CTR, nonce=nonce)
CTR_ENC.encrypt(m1).hex() + CTR_ENC.encrypt(m2).hex()
# <=>
CTR_ENC.encrypt(m1 + m2).hex()
Exploitation :
We use the property of CBC to find the cipher of the block by CTR
Adfter the first encryption, the state of CBC is :
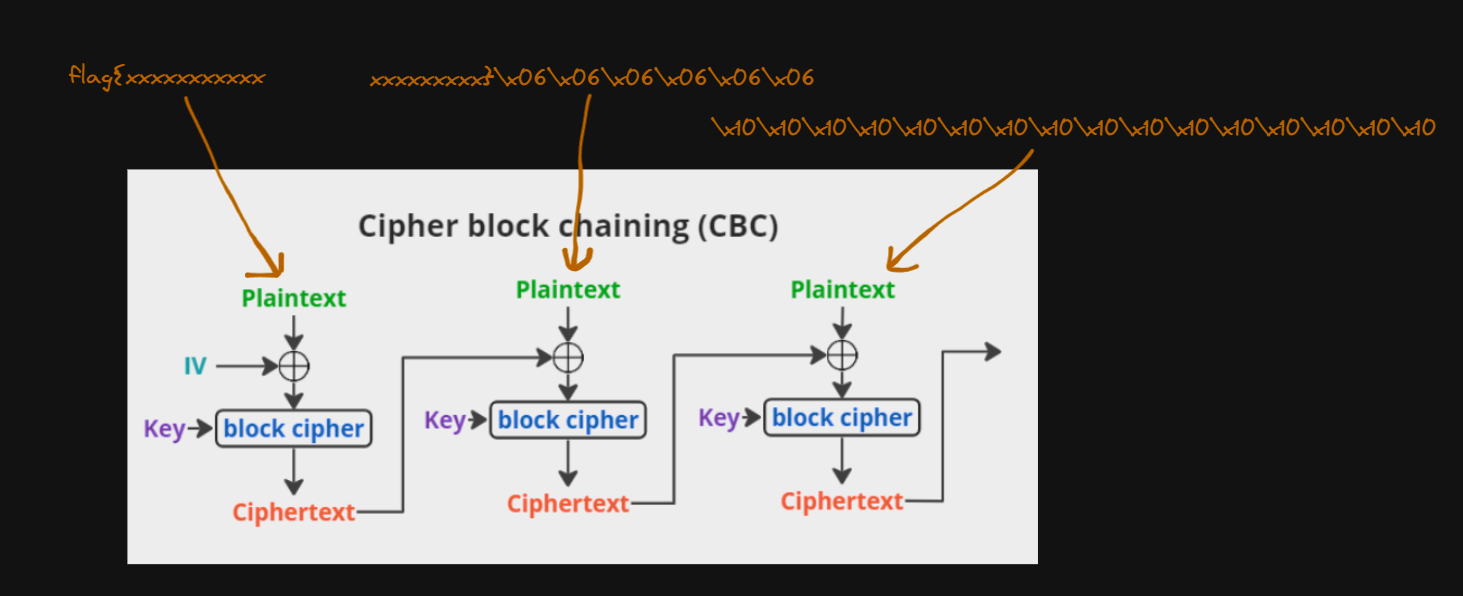
So, we know C3, the third block of the cipher text of CBC.
But in parallel, we have the same thing for CTR :
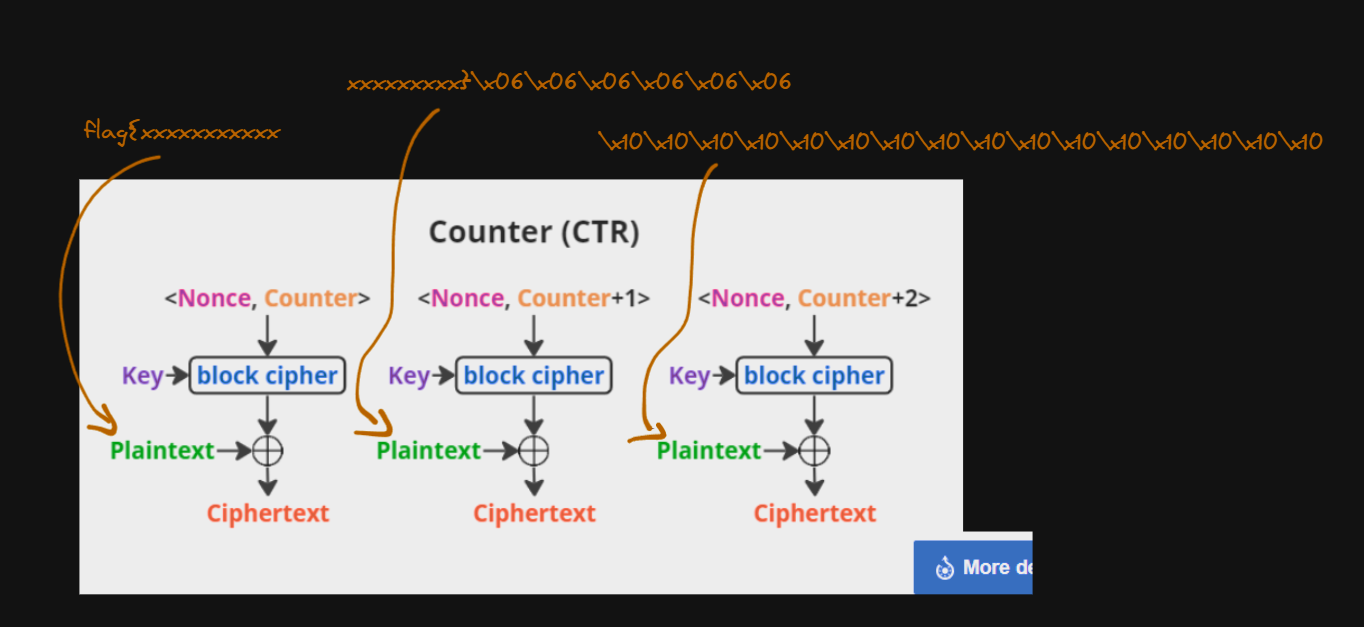
For CTR, we know the nonce, its for exemple : 0x01234567
Imagine we know the key, if we have the key and the nonce, we can compute Enc_CTR(Nonce + i), and with the ciphertext, we can retrieve the plaintext.
Pay attention to the CBC methode, we can compute Nonce + i in CBC mode with the good input like this :
To explain how CTR works with the nonce, it is very simple. When you give a nonce of 8 bytes, the nonce given to the AES is : Nonce\x00\x00\x00\x00\x00\x00\x00\x00 or "01234567" + "\x00" * 8
The counter increase by 1 for each block. So, the first block is Nonce + 1, the second is Nonce + 2 and so on.
The best way to be sure of that, is to test it with the simple ECB mode
import os
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad, unpad
from Crypto.Util import Counter
nonce = os.urandom(8)
iv = os.urandom(16)
key = os.urandom(16)
CTR_ENC = AES.new(key, AES.MODE_CTR, nonce=nonce)
ECN_ECB = AES.new(key, AES.MODE_ECB)
def xor(data1: bytes, data2: bytes) -> bytes:
if len(data1) != len(data2):
raise ValueError("data1 and data2 must have the same length")
return bytes([b1 ^ b2 for b1, b2 in zip(data1, data2)])
def ctr_encrypt(data):
print(pad(data, 16))
return CTR_ENC.encrypt(pad(data, 16)).hex()
flag = pad(open(file_path, "rb").read(), 16)
ctr_enc_flag = ctr_encrypt(flag)
block1 = ctr_enc_flag[:32]
block2 = ctr_enc_flag[32:]
b1 = bytes.fromhex(block1)
b2 = bytes.fromhex(block2)
print("Enc(Nonce) : ",xor(b1,flag).hex()) # Enc_CTR
print("Guess Enc(Nonce)", ECN_ECB.encrypt(nonce + b"\x00" * 8).hex()) # Enc_ECB("01234567" + "\x00" * 8)
# We can see, it's the same
print("Enc(Nonce) : ",xor(b2,b"\x10" * 16).hex())
print("Guess Enc(Nonce)", ECN_ECB.encrypt(nonce + b"\x00" * 7 + b"\x01").hex())
If we know Enc_CTR("01234567" + "\x00" * 8) we can find the first part of the flag, meaning flag{xxxxxxxxxxx
Okay, now we have all the information needed to retrieve the flag.
Solution :
from pwn import *
def xor(data1: bytes, data2: bytes) -> bytes:
if len(data1) != len(data2):
raise ValueError("data1 and data2 must have the same length")
return bytes([b1 ^ b2 for b1, b2 in zip(data1, data2)])
def xor_hex(data1: str, data2: str) -> str:
return xor(bytes.fromhex(data1), bytes.fromhex(data2))
conn = remote('vsc.tf', 5000)
ctr_enc_flag = conn.recvline().decode().strip()
print(ctr_enc_flag)
cbc_enc_flag = conn.recvline().decode().strip()
print(cbc_enc_flag)
nonce = conn.recvline().decode().strip()
print(nonce)
cbc_enc_flag_new = cbc_enc_flag
message = ""
for i in range(4):
last_block_cbc = cbc_enc_flag_new[-32:]
plaintext_to_found_nonce = nonce + "00"*7 + str(i).zfill(2)
print(plaintext_to_found_nonce)
assert len(plaintext_to_found_nonce) == 32
payload = xor_hex(last_block_cbc, plaintext_to_found_nonce).hex()
print(payload)
assert xor_hex(payload, last_block_cbc).hex() == plaintext_to_found_nonce
conn.sendline(payload.encode())
ctr_enc_flag_new: str = conn.recvline().decode().strip()
cbc_enc_flag_new = conn.recvline().decode().strip()
print(ctr_enc_flag_new)
print(cbc_enc_flag_new)
enc_block_ctr = cbc_enc_flag_new[:32]
plaintext = xor_hex(enc_block_ctr, ctr_enc_flag[(i)*32:(i+1)*32])
print(plaintext)
message += plaintext.decode()
print(message)
Flag
vsctf{me_wen_cbc_6c855453171638d5}